There are several ways to find a person using a photo on the Internet.
Similar articles
EDS update for 2021
Digital signature for a legal entity
Load more
Before you start searching by photo, you need to get a “portrait” of the stranger. A portrait in our case is a photograph of the face of the person of interest. If you are looking for a person in a group photo, you should crop it, leaving only the person you are looking for. This will increase the speed and accuracy of the search.
You can find a person by photo on social networks, the only thing is you need to know which one to look for. There are special services, for example, for VK and Odnoklassniki. For networks that strictly monitor the safety of personal information, it is almost impossible to find such services.
A simple, but at the same time, in my opinion, the best search method is search engines. Advanced search engine algorithms perfectly analyze images and find similar pictures.
How to find out the location from a photo? How is this even possible?
The easiest way to get information about a person that he himself posted on the World Wide Web is through his photographs. Modern search engines can search for photos similar to the one provided and even determine what exactly is shown in the photos, thanks to artificial intelligence. The main thing is that the graphic file is in the public domain and is indexed by search robots.
A photo search starts with Google Images (you can also try Yandex.Images and TinEye), but the photograph should not be heavily processed in a graphics editor, otherwise the search algorithms will not give the required result. The picture is uploaded to the server to search for similar ones, or a direct link to the file is provided. As a result, it will be possible to find similar images and, perhaps, even the name of the person depicted on them. In a similar way, it is quite easy to find a person’s page on social networks.
How to find a person by photo using Yandex.Images
- Go to https://yandex.kz/images/
- Click the camera icon
- In the "overlay" window:
- First tab - you can drag a file from a folder, or specify the location by clicking “Select file”
- Second tab - you can enter the address of the photo and click “Find”
- There will be links under similar images. Look for profiles on social networks. You can go through the photos.
Yandex searches for pictures very well, but for a high-quality definition, it is advisable to use both search engines.
Can you be tracked using your photo? How to avoid this?
To prevent personal photos from spreading across the World Wide Web, simply do not upload them to it. Only a few are actually ready for such radical measures, which means that care must be taken to ensure that photographs are not indexed by search engines, that is, they are in personal albums and are accessible to a limited circle of people. Avatars used in instant messengers should be made visible only to users from the contact list.
Where possible, add a watermark, which is translucent information placed on top of the main information, especially when it comes to documents. It is best to apply watermarks in a photo editor installed on your computer, rather than uploading the photo to a remote server for online processing.
If possible, upload unique photographs for each messenger and Internet resource, process them in photo editors - thanks to this, it will be much more difficult for search engines and other services to determine the person captured in the photograph. Display minimally sized pictures for everyone to see. The less detailed a photograph is, the more difficult it is to recognize. For example, in the case of Instagram, this is quite difficult to do, otherwise you can lose subscribers, and the growth rate of their number will significantly decrease.
If possible, use different nicknames and last names on different sites, and do not link Instagram to Facebook.
Use the ability to log in to sites via social networks to a minimum. Internet resources may request access to personal data, including photo albums. After which they were repeatedly released into the public domain. In particular, the NameTests service has long kept information about 120 million authorized users publicly available.
Saved photos in VK from your phone
Adding photos to VK saves from a mobile device is just as easy. Just open the picture/photo, click on the ellipsis in the upper right corner and click on the inscription “Save to album”.
All saved photos are stored in a special album. Here you can view or delete them.
- By the way, if you click on the “Save” button, the photo will be uploaded to the phone in the gallery (folder “Dowloads”);
Hide VK saves
It's not difficult. In the settings, open the “Privacy” section and in the “Who can see the list of my saved photos” column, indicate the desired value.
What can you learn from photo metadata? Why should you remove metadata?
Do mobile apps really spy on users?
Many have noticed that after uploading photos to social networks, these Internet resources somehow find out about the place where the photo was taken and offer to mark it on the map. Smartphones and tablets automatically add GPS coordinates to photos of the places where they are taken. This information is commonly called metadata or EXIF, and social networks understand it. In addition to coordinates, they may include the time and date of shooting, the model and manufacturer of the smartphone/camera, as well as other technical information.
There are known cases when Google automatically created photo albums of Android users from photos taken while traveling or on vacation, based on a changed daily routine, geolocation data, and information from the GPS device.
The social network Vk manages to monitor absolutely all the events that happen in the world. How? Of course, thanks to us - ordinary users who publish photos from all over the globe. There is a whole ocean of varied information on VK.COM. But it can be difficult to look for something specific there. On every corner there are reposts of funny pictures, selfies, advertisements for sushi delivery, prize draws and other spam.
But there are simple, but not obvious, search techniques that will help resist evil. Since you are not the only person who is familiar with this option, next to your photos there may easily be photos of other people who can easily be viewed based on location.
When you publish a photo, VK automatically records the geolocation where the photo was taken. Using this method we can get a list of photos taken at a specific location.
1. Find out the coordinates of the place using the Google Maps service. 2. Go to https://vk.com/dev/photos.search and look for “Example request” there 3. Fill in the required fields in the request: lat and long - geographic latitude and longitude start_time - time in unixtime format, not earlier than The found photos had to be uploaded. end_time — time in unixtime format, no later than which the found photos should have been downloaded. sort — sorting the results. 1 – by quantity o; 0 – by date the photo was added. count — number of photos returned. radius — search radius in meters.
In the response we will receive an XML structure with a list of photos. For each photo, information such as: owner_id - VK user ID will be available; lat and long are the exact coordinates of the photo;
Links to photographs in different sizes will also be included.
If you still don’t understand why this option is needed, then think about how you can use it to look for new friends, how you can view the beauty and landscapes of the places where you are planning to go on vacation... You see, it’s not so pointless to look for other people’s photos according to their geographical location!
Disclaimer: The author or publisher has not published this article for malicious purposes. All information posted was taken from open sources and is presented for informational purposes only and does not contain a call to action. Created for educational and entertainment purposes only. All information is aimed at protecting readers from illegal actions. The visitor assumes all possible damages caused. The author performs all actions only on his own equipment and on his own network. Don't repeat anything you read in real life. | Also, if you are the copyright holder of the material posted on the pages of the portal, please write to us via the contact form with a complaint about the deletion of a certain page, and also read the instructions for copyright holders of materials. Thanks for understanding.
- Cisco Packet Tracer – Young Soldier Course
The specificity of the work is such that a system engineer in a very short time... - Manual for restoring MikroTik firmware over the network via Netinstall
If, after updating the firmware, the MikroTik access point or router stops... - About the intercom keychain and can it be used as a flash drive?
The key to the entrance intercom works simply: put it in and the door... - How do scammers send SMS spam? What are the main advantages of SMS mailings?
Today we will look at this type of traffic attraction as... - How to make money selling gaming products
Every human activity involves sales. At school they sell us knowledge... - etl files in Windows: what are they? Can be deleted?
ETL stands for Event Trace Log file, which is created by Microsoft Tracelog, a program that... - How to create phishing sites in 5 minutes
Phishing is one of the easiest ways to obtain personal data... - How to create commercials or video ads
As you know, “advertising is the engine of trade.” The authorship of these lines is attributed to... - The Art of Deception: Literature and articles on psychology, SI, emotions and so on
By becoming victims of deception, we not only put ourselves at risk, but... - How antiviruses sell your browser history. Secret market for trading personal data
An antivirus program used by hundreds of millions of people around the world... - Reverse engineering of microcircuits or how to copy a microcircuit using a microscope
Microcircuits are still copied today in different countries. Manufacturer of original chips… - How to upload reverse-shell to WordPress site
In this guide, we will present you with all the ideas to... - Hack Google Audio reCAPTCHA using Google's own speech-to-text API
Many sites now use recaptcha from Google and for good reason:... - How to unsubscribe from all channels with one click on YouTube
I think everyone knew about this method, but still, some... - Review of processor sockets: detailed descriptions of generations with photographs
First, we need to stipulate that in order to clarify the markings and characteristics... - How to catch scammers for illegal activities online
The most pressing issue is the compilation of the evidence base. Therefore, the arrest of the attacker... - SIM bios: how scammers make duplicate SIM cards
In our age, technology is developing more than rapidly and every... - Web cache poisoning via host header injection
Header Host Injection is a vulnerability in its brief description, it is... - About how scammers blackmail and extort money from Ukrainians through Facebook and Telegram: how to avoid becoming a victim of deception
In Ukraine, cases of theft of pages on social networks have become more frequent and... - A selection of top courses of information products and other goodies (large collection)
Sometimes a school and university program is not enough to become competitive in...
How to check and remove metadata from photos?
How to find out if a site has vulnerabilities
To check and remove metadata, you can resort to third-party utilities or use built-in Windows tools. In the second case, just open the properties of the photo and visit the tab with meta-data (it’s called “Details”). In it you will find a lot of technical information, information about the device that created the photo, and, possibly, the coordinates where the photo was taken.
Such information can be seen and deleted through any pixel graphics viewer installed on your computer, for example, FastStone Image Viewer.
To get rid of EXIF data, on the “Details” tab, click the “Remove properties and personal information” button.
Brute force is terrible power!
Move the switch to the “Remove the following properties for...” position, check the boxes for unnecessary information, or click the “Select All” button, then “OK” in both windows.
This technique also applies to several files located in the same directory.
Tips and conclusions
Photos uploaded to the World Wide Web can sometimes tell a lot about a person and even lead to his pages on social networks. Search engines can even recognize an avatar used on a forum or messenger.
To avoid this, minimize the distribution of personal photographs in any form. When you need to showcase a photo album, limit access to it, and don't forget to remove meta data. But if you send photos via instant messengers, almost all of them remove metadata from the photo automatically.
How to hide saved photos on VKontakte
If you want to open
or
hide saved photos in VK
, you can do this in the “Settings” section, “” tab.
Select the required value in the column.
If you want to delete saved photos
or
transfer them to another album
, then first go to the album with the saved files.
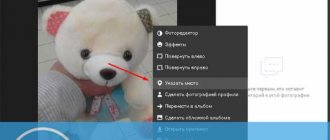
- Under the photo, you can click on the “Delete” or “More” button to move it to a separate album;
If you want to delete all saved photos in VK
in one action, then this will not work. At the moment there is no working extension/application/script. And do not try to use fraudulent programs for this - there is a chance of being hacked.