Smart TV
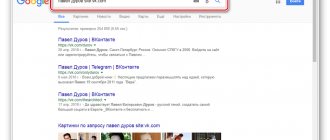
You've probably already heard that today you can get information about almost any person through social networks
, and especially through VKontakte. Moreover, very often it is not at all necessary to be registered in it. It is enough to type the last name, first name and city of residence of the desired person in the search engine and that’s it.
I won’t go into detail about why this is bad (anyone who wants to can read the article I wrote on this subject about protecting a VKontakte account), but I’ll focus on how to make life even a little more difficult for curious people.
How to block your contact page from search engines? (Yandex, Google, etc.)
In the upper right corner click on the avatar. Select " Settings
».
Select the “ Privacy”
"
Scroll down to the “ Other
” block. Opposite the line “Who can see my page on the Internet” set the value “”.
If you have the old VKontakte design active
Go to the “ My Settings”
", the "
Privacy
" tab and opposite the very bottom line "Who can see my page on the Internet" set the value to "
Only VKontakte users
".
To check if you did everything correctly, do the following. Select “ My Page”
", then click on "
Log Out
".
After this, the following message should appear. « The page is available only to authorized users
».
The page is available to authorized VK users
Hello! Today we will look at the meaning of the warning: “The page is hidden. The page is available only to authorized users."
More recently, the social network VKontakte was closed, i.e. the content was not indexed by search engines. Webmasters immediately took advantage of this, using parsers to pull discussions from the social network and fill their sites with them. The same applied to profiles - information from them was also taken without the knowledge of those registered on the social network.
The modified version will be effective from the 6th day after the specified notification is sent. If you object to the updated Agreement, you may elect to terminate the Agreement by written notice in accordance with Section 18 of this Agreement. The parties are independent contractors; This Agreement shall not be construed to constitute either party as a partner of the other or to create any other legal association that would give either party the express or implied right, power or authority to create any obligation of the other party. All notices under this Agreement must be in writing. Notices sent will be deemed received on the first business day in Quebec, Canada after we send them. You may not assign this Agreement without our prior written consent. We will not waive our consent if the recipient agrees to be bound by the terms of this Agreement. We may assign our rights and obligations under this Agreement without your consent. If any provision of this Agreement is held invalid, void, unenforceable or illegal, the remaining provisions will remain in full force and effect. This Agreement may not be amended or modified by you without our written consent. No default or delay on the part of the aggrieved party hereto in exercising any right, power or privilege hereunder shall be construed as a waiver of that right or shall deprive him of any other right or remedy under this Agreement.
- We may notify you by email or through your account.
- Your opinion will be considered received upon our reception.
Use the tables and information below to determine what permissions to grant to users.
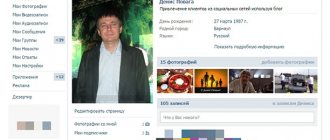
It was impossible to fight the emergence of such sites, and the owners of VKONTAKTE took radical measures - they opened a social network for indexing. Immediately, tens of thousands of groups and millions of users appeared in Yandex and Google. Not everyone liked this. Imagine that someone entered your first and last name in a search and immediately came across a VKontakte profile, where almost all personal data is often indicated.
These permissions appear in separate sections of the dialog box. In the basic version, the administrator role is assigned to all users. Account administrators can add, delete, and edit user accounts across all products available for the account. They are also allowed to change billing and product configurations.
Administrators can add other user accounts, set permissions, and access all dashboards, apps, tools, analytics, and settings. You can grant this user Write, Publish, Write, or Read Only permissions for each content tool: blog, landing pages, website pages, and email. Please note that to enable workflows, the user must have permission to write and publish email. Marketers have the same level of access as administrators, but cannot add user accounts or set other users' permissions. Please note that to enable workflows, the user must have permission to record and publish emails. You can grant permissions to this role for write and publish, write-only access, or read-only access. They can also assign tasks to other users. Below you will find more information about user roles and permissions.
Therefore, it was decided to add an item to the privacy settings - “who can see my page on the Internet” with the following options:
- Only VKontakte users
- Everyone except search sites
“If you hide a page from search sites
, it cannot be found in an Internet search.
For example, in Yandex or Google. Search engines store the collected data for some time. Therefore, the page will not disappear from the search results immediately
and may be available in searches for up to one month.”
Adding reports
Advertising module
- However, they cannot set default portal properties.
- Administrators can change the owner of any team's dashboard.
If you don't assign any permissions to any of the products, the user account is deleted.
Users must have access to at least one product to remain active. Additionally, you can revoke access to third-party services and security tokens if necessary. In this section, you can view the security tokens entered by the user. Add a security token to the user by clicking Add new token. Users who register this way do not have to provide their phone number for security token registration. Let me explain a little. Despite the power of search engines, the results are not updated immediately, but during so-called “updates”. Yandex needs about 2 weeks, Google a little less. So don’t think that as soon as you block visibility in search engines, your page will immediately disappear. Unfortunately no.
All options are set on the page (https://vk.com/settings?act=privacy) My settings —-> Privacy (other tab).
In the section Work of the authorized access operator. You may only revoke access to a service once it has been provided. You can't prevent users from granting access to certain apps in advance. If an authorized user cannot verify their identity, click Disable Access Verification. Access check will be disabled for 10 minutes to allow the user to login.
The profile contains user settings. An organization can hide bibliographic information as part of its security settings. It is also possible to change bibliographic information and authorized users to view a profile based on your organization's security settings. Only organization administrators can change the email address.
Now, when trying to view your information, an unauthorized user will see the following message:
But unfortunately, VKontakte has one loophole through which a person who is not registered on the social network can find the desired profile. networks.
To change your profile, make sure you have access, click your name at the top of the site screen and select the My Profile link. The profile page will be displayed. Click the Edit Profile button and update one of the following settings. The name appears at the top of the profile page when someone clicks on the username. Your username appears in the details of groups and your content.
You can change the name, while the username cannot be changed. Adding bibliographic information about yourself allows other users to know some personal information, groups they participate in, and general content. Personal interests listed in your profile allow you to connect with other users who have similar interests and they can indicate their own level of experience with geographic data, map design, app development, etc. Profile information can also serve to post your groups and highlight shared maps and apps. It is useful to include contact information and areas of specialization and interest.
You will be able to see an avatar, a city, an educational institution. But when you try to go to the full profile, you will still see the error - “The page is available only to authorized users.”
Now you know why this message appears. Have a good day!
It's also helpful to include a "preview image, such as your own photo, logo, or other" image. The formula for successful sites and their good users is planning and a sustainable approach to site and user management. Here are some key tasks and concepts you can use to plan your organization's sites and manage users.
Site collections are hierarchical and always include a primary site and any secondary sites. The Site Site, and any sites created within it, are accessible only to users who have Site permissions. With a team site, an organization, team, or workgroup can continue to connect and collaborate on documents and other files, post announcements, schedule meetings, manage events, track issues or obligations, store information in lists, and more. You can also create multiple subsites from the site templates available on the team site.
This article uses a desktop application in Java as an example, but the general principles and scheme will be similar for any other language.
How does authorization occur?
Authorization on VKontakte is no different from any other authorization through a third-party server. This process was perfectly described by StackOverflow user qnub
:
Typical Responsibilities of Site Site Administrators
This way, you can delegate site or site management to multiple users in an organization. Administrators are also allowed to view, add, delete or edit any content on these sites. View, delete or restore items from the site's Harvest Recycle Bin. Create and customize your public website. Provide administrative support for certain features, such as: Enable or disable features available for a site collection, Create or configure site content types, Configure international settings. Activate or deactivate an external resource.
Typical Responsibilities of Website Owners
- Determine what features are available to site users in the collection.
- Provide technical support to website site users.
- Select an additional site administrator for the site collection.
- Create, delete, and manage site collections.
- Allocate and manage storage for a site collection.
- Grant access to site collection administrators.
- Plan and manage features such as managed metadata.
The responsibilities of site owners who have the Full Access permission level for a site include the following.
- On the service (in this case VK) you need to register the application and receive an API key.
- After this, the application (site) can request the user’s personal data from a third-party service through this same API, for which:
- redirect the user (user's browser by sending him a 302 Redirect HTTP response) via a specially generated link
to a service providing an API; - the user will perform some actions there, presumably log in and allow access to the data.
- Upon completion of the actions, the user will be redirected by a third-party service using the same 302 Redirect to the URL passed in the parameters of a specially generated link
.
Step one. Register your application and get a key
This step is the easiest. You need to go to the VK page for developers: https://vk.com/dev - and click on the “Create an application” button. We indicate the type as “Standalone application”, the name, of course, is arbitrary. After that, your application will appear in the “My Applications” section (what do you think?) Feel free to click “edit”, then go to the “Settings” section - there in the first line you will see the inscription “Application ID: 1234567
" These numbers are all you need to remember to log in.
Manage site features and settings, such as appearance, managing columns and content types, setting international settings and language, and listing site templates. The following list includes supported site templates and a short description of each. Refer to this list to determine which types of sites are most suitable for your organization. Includes pages for search results and advanced search. manage storage, search and export of content for legal issues and surveys. Document Center. Center for centralized management of business documents. Center for organizing research to provide search functions. The home page has a search box with two tabs - the General Search tab and the Search User Information tab. You can add and customize tabs to focus on other search areas or result types. Project website A site for managing and collaborating on a project. The site record is for managing records. Record managers can set up a table to route incoming files to specific locations. You can add other web pages related to the workflow. Contains a set of documents and lists for managing announcements, calendar items, tasks, and discussions. It also provides a versioned document library for storing process diagrams, as well as lists for managing announcements, activities, and discussion threads. Core Research Center to provide search functionality. . The term "governance" refers to the set of rules, roles, responsibilities and processes that guide, direct and control collaboration between technical teams and business units of an organization to achieve business goals.
Note that there is no point in hiding the application ID - it is publicly displayed, for example, when posting a wall message through this application. Neither tokens nor any other information can be stolen using an ID. In fact, you can even use my application ID (if you need to write a small script for yourself).
Step two. Generating a special link
Next, you need to direct the user to a specially generated address (its mentions are highlighted in bold in the first section of the article), where he will confirm that he wants to allow your application to perform some actions with his account. How is this link formed?
This process is described in detail in the documentation. However, if you turned to this article, I assume that you did not have enough information in the documentation, and therefore I will retell everything in my own words. The link looks like this: host?parameters. The parameters take the form of several key=value pairs separated by & symbols.
The host always remains the same: https://oauth.vk.com/authorize. The set of parameters is also unchanged:
- client_id
. Here it is worth indicating the same numbers that we obtained in the first step. - redirect_uri
. The address to which the user will be redirected. For Standalone applications this is only https://oauth.vk.com/blank.html. - display
. This parameter determines how the login page will be displayed. There are three options available: page, popup and mobile. If you're not sure, use page . - scope
. In this parameter, you should list the access parameters that you need, separated by commas. A complete list of available parameters is provided on the corresponding documentation page. Please note that you don’t have to specify anything at all and just don’t write this parameter. To find out what access options you need, look at the documentation of the methods you are going to use. - response_type
. We specify the token and move on. - v
.
API version. Current – 5.59
.
https://oauth.vk.com/authorize?client_id=1&display=page&redirect_uri=https://example.com/callback&scope=friends&response_type=token&v=5.59
Step three. What's next?
https://REDIRECT_URI#access_token= TOKEN
3&expires_in=
TIME
&user_id=
ID
We are interested in TOKEN
. How to direct the user to a page from a Java application and how to get the address of the page to which VK will redirect him (in order to extract a token from it)? There are two ways.
If you decide to go this route, then you simply open the system's default browser with the link you received above, and somehow tell the user that he should copy the token from the URL and paste it into some field. Obviously, this method has terrible UX, but it can be implemented quickly and easily. It is quite suitable if you are writing an application for yourself - to download music or receive notifications. It is implemented as follows:
Public String askToken(String link) throws IOException, URISyntaxException{ //Opens link in default browser Desktop.getDesktop().browse(new URI(link)); //Asks user to input token from browser manually return JOptionPane.showInputDialog("Please input access_token param from browser: "); }
Bourgeois, via web components
If you decide to go this route, you will need to use some third party GUI library (or at least JavaFX) that has its own browser component. Your program will have full power over such a browser, and you will be able to retrieve the address to which VK redirected you using software. In JavaFX this can be implemented as follows:
Import javafx.application.Application; import javafx.beans.value.ChangeListener; import javafx.beans.value.ObservableValue; import javafx.scene.Scene; import javafx.scene.web.WebEngine; import javafx.scene.web.WebView; import javafx.stage.Stage; public class Main extends Application{ public static final String REDIRECT_URL = "https://oauth.vk.com/blank.html"; public static final String VK_AUTH_URL = ""; //TODO!!! public static String tokenUrl; public static void main(String args){ System.out.println(Main.getTokenUrl()); } public static String getTokenUrl(){ launch(Main.class); return tokenUrl; } @Override public void start(Stage primaryStage) throws Exception { final WebView view = new WebView(); final WebEngine engine = view.getEngine(); engine.load(VK_AUTH_URL); primaryStage.setScene(new Scene(view)); primaryStage.show(); engine.locationProperty().addListener(new ChangeListener(){ @Override public void changed(ObservableValue extends String> observable, String oldValue, String newValue) { if(newValue.startsWith(REDIRECT_URL)){ tokenUrl=newValue; primaryStage.close( ); } } }); } }
Conclusion
Thus, we learned how to obtain a VKontakte access token, with which you can call API methods. If this article arouses interest in the community, in the next article I will describe how to call certain API methods using a token, how to check the validity of a token (the secure.checkToken() method, of course), and write some kind of demo application, for example, to save all the music from a playlist to your computer. By the way, do not forget that in fact everything was invented before us, and there are already libraries for working with the VK API for almost any language. We have, in which we tried to collect the best of them.
If you have any ideas or questions, welcome to the comments (I read them and answer everyone). You can also ask questions
How to close your VKontakte page from other users?
You can close the entire page, or some part of it, from VKontakte participants in the same way - by going to the settings section, the “ Privacy”
" and setting the settings properly.
(Most often in the meaning “ Only me
”). Each item is described in detail, so you can figure out what is responsible for what.
The vast majority of sites are freely accessible and free for users. However, there are resources that offer additional information and subscription to paid services that require a procedure such as authorization. What does this give to users?
The user needs to fill out a form to create a domain with a personal login and password. A login is a unique name that is presented to a user on a given site. Typically, there cannot be two identical logins on one site. As for the password, it is a coded secret word or a certain sequence of characters. It confirms the fact that you are the owner of this login. For security purposes, when you enter your password, it is displayed with asterisks. There are sites that offer you to choose your own login and password, while others generate them yourself.
What are the types of authorization errors?
An authorization error is an incorrect entry of the username or password for the service. If this happens, the system will indicate that the login or password was entered incorrectly. In order to solve the problem, you need to make sure that you are entering the correct data, eliminate errors, perhaps a character was missed, and also check the keyboard layout and the caps lock key, which makes all characters capitalized.
Look at the material on the topic: “How to come up with a strong and memorable password.”
If you have checked all the data according to the above recommendations, but the system still does not allow you to log in, then most likely you have forgotten your password. In this case, a solution is also provided. Just click on the “forgot password” button, and the system will reset your old code and offer to come up with a new one if you confirm that this is really your account. As a rule, password reset occurs either through the phone number associated with the site, or through the mailbox attached to the service.
What can happen if there is an authorization error
- The system will record the fact of unauthorized access;
- The system will notify the user of the error with a signal or notification on the screen;
- For security reasons, the system will restrict access to the entrance for a while;
- The system will prompt you to re-enter the data several times;
- The system will prompt you to reset your password and set a new one;
- The system will prompt you to register again;
- The system will block the account, bank card or electronic time recording pass.
Authorization - what is it?
User authorization is a fundamental function on many websites. A typical Internet user encounters it regularly: on social networks, on forums, on news sites when leaving comments, on banking websites. As previously mentioned, when registering on the site, you can take advantage of the additional functions and capabilities provided. For example, in social networks it is an opportunity to see other profiles, communicate, download information, and in online stores it is possible to select and order any product.
What does it mean to log in to a website using Yandex as an example?
The concept of authorization is becoming more and more common in the modern world, so you need to know what it means to log in when a message appears that says “authorization required.”
Let's look at the authorization process in Yandex step by step:
- If you open the Yandex home page by default, then in the right corner click on the “Login to mail” button:
- If another search engine is open, then enter “Yandex mail” into the search and open the first link, this should be the official website. Or follow the link https://mail.yandex.ru/.
- In a special window, you will need to first enter your login and then your password. Enter your data if you are registered on the site. Next, click the login button. Authorization completed.
- If you are not registered, click on the registration button, fill out all the required fields, create a username and password, and remember them. The process of creating Yandex mail is described in detail at the link
- After successful registration, log in to the site as described in point 3.
After completing these five steps, you will be able to log in to Yandex.
You will need to do a similar procedure for entering your login and password on many sites where you want to perform an action, but cannot. The system will ask you to enter your login information. This process is requested on almost every website, forum, online stores, and social networks. This gives users some privileges, for example, authorized forum participants can leave their comments, and not just read the correspondence of other users, and after logging in to a social network, you can also view people’s profiles, add to your friends list, subscribe, and write messages.
In online stores, only authorized users can place an order, because during registration they indicate their contact information and address.
Now you know what authorization on the site is, so don’t be alarmed when the system asks you to log in, this is the normal procedure for logging into your account.
Why is user registration needed?
As you understand, identification helps to identify a site visitor, as well as to impose restrictions on its capabilities and resources for other users.
The question arises: authorization - what is it and why limit access using it? After all, it would be much easier to provide the site's capabilities to all users. Moreover, the registration procedure sometimes takes quite a bit of time. But there is one good reason why owners introduce authorization. The fact is that it helps to limit visitors and the site itself from spam. Another important purpose of authorization is identification.
This information is transmitted voluntarily and is used solely for the purpose of recognition by other visitors.
Naturally, registration has many other tasks and functions, but these two are the most important.
What to do if you forgot your login or password
Enter your access data, and the response is “Incorrect login or password”? Perhaps you simply forgot one of the authorization combinations, or maybe the attacker changed them intentionally. It's okay, we'll try to recover the password automatically.
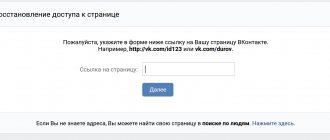
1. Go to the page - https://vk.com/restore.
2. Enter the phone number or email address to which the account was registered. Click Next.
3. Enter the last name listed in your profile.
4. Select your account from the list provided and click “Yes, this is the right page.”
5. An SMS with a verification code will be sent to the specified number.
6. At the end, you will be asked to create and save a new password.
If you do not have access to a phone number, enter your email or find the desired profile through the search, by First Name and Last Name, using the links provided.
Main advantages of identification
Both site owners and its users have benefits. The advantages for the owner are:
- Anti-spam protection (screening out spam bots).
- Restriction of rights to use additional services. For commercial sites, authorization is simply necessary, since they provide their services for money.
- The ability to get to know the user, which also has its advantages: geographic, demographic and other information about visitors, which allows you to set up the site correctly, select the most effective advertising and keywords.
Benefits for users:
- Also anti-spam protection.
- Ability to recognize your interlocutor.
- Additional features such as filling out a profile, uploading a photo, other files, and so on.
So, we figured out what authorization is. That this is a means of protecting user data. For websites it is of great importance. Based on this, you should take the situation seriously if your authorization fails.
Go to the VKontakte website https://vk.com/. In the address bar (at the top of the window) put “/” and write search. Press Enter.
Step 2
A search window will open. In the line, enter the first and last name of the person whose page you are looking for. If there are many people with the same name, fill out the advanced search form on the right.
Step 3
You go to the page and look at it. What to do if “The page is available only to authorized users.”? There is a solution! Do you know who has this person as a friend? If so, find a “middleman.” For example, you searched for Vasya Pupkin, and his “Page is available only to authorized users.” Vasya is a friend of Ololoshi Ololoev. So, look for this Ololosha Ololoev.
Step 4
Once you find him, look at his friends list. Have you found the person you need? Hover over his photo and click “Enlarge”. Below the photo you will see this (look at the picture). Click on “Photos from Page...”. A window will open with all the photo albums of the person you need.
How to restore a blocked page
The reason for blocking is always a violation of the user agreement
, which is accepted upon registration. The most common reasons:
- Spam;
- Complaints from other users;
- Uploading content that contradicts the legislation of the Russian Federation;
- Creating a profile of a non-existent person.
If you did not abuse the rules, and your profile was hacked, familiarize yourself with the rules of online behavior; most likely, their simple ignorance led to this situation.
Account recovery is always free. If you are asked to send an SMS to a paid number, your computer may be infected with a virus
. To solve the problem, check your PC for viruses.
1. Go to the website vk.com. Log in using your old username and password.
2. A notification about temporary blocking will appear.
3. Enter the phone number that was specified during registration.
4. After receiving an SMS with a code, write it down in a special form.
5. Create a new, complex password using our instructions. This will protect your profile in the future.
If your account is permanently blocked, you need to write a request to support. We will discuss this point in more detail later.