How to view the page code?
To view the source code of a site page, you need to hover your mouse over any area of the web page (except for images and links). After this, click on the right mouse button. A window with several options will open in front of us (they may differ slightly in different browsers). In the Google Chrome browser, for example, these are the commands:
- back;
- forward;
- reboot;
- save as;
- seal;
- translate to Russian;
- view page code
; - view code.
We need to click on view page code
, and the html code of the site page will open in front of us.
Other ways to use this feature in the Google Chrome browser
In general, continuing to answer the question of how to look at the code of an element and why it is needed, you should list its functions. Namely, thanks to the ability to view the code of an element of any site in the Google Chrome browser, we can:
- See the structure of the site starting from head (“site header”) and ending with end (the final command of any program);
- View all the functions of the site, namely: links to other sites, additional modules from external sites and the presence of built-in counters for collecting various information;
- Find out whether copying from the site is prohibited or not;
- The code will record all links to other pages of the site, as well as their design and subsequent actions after clicking on them.
This is by no means a finite list. But it should be recalled that without special knowledge, it is almost impossible to “read” the code of a Google Chrome page and the received data is practically not needed by an ordinary user.
Viewing the page code: what to pay attention to?
So, the Html page code is a numbered list of lines, each of which carries information about how this site is made. To quickly learn to understand this huge number of signs and special symbols, you need to distinguish between different sections of the code.
For example, lines of code inside the head tag contain information for search engines and webmasters. They are not displayed on the site. Here you can see what keywords this page is promoted for, how its title and description are written. Also here you can find a link, following which we will learn about the family of Google fonts used on the site.
If the site is made on CMS WordPress or Joomla, then this will also be visible here. For example, this area displays information about a WordPress theme or Joomla site template. You can see it by reading the contents of the links highlighted in blue. One link shows a website template.
For example:
//fonts.googleapis.com/css?family=Source+Sans+Pro%3A400%2C400italic%2C600&ver=4.5.3
We will see the CSS font styles of the page. In this case, the font is used. You can see it here - font-family: 'Source Sans Pro'.
This site is optimized using the Yoast SEO plugin. This can be seen from this commented section of code:
This site is optimized with the Yoast SEO plugin v3.4.2 - https://yoast.com/wordpress/plugins/seo/
All information contained inside the body tag is displayed by the browser on the monitor screen. Here we see the html code of the page, and at the very bottom there is the Yandex Metrics script code. It is surrounded by a commented tag with the text:
/Yandex.Metrika counter
Hidden text
Recently, more and more often, the source code of scripts is encrypted or packaged. Yandex, DLE and other popular projects began to get carried away with this, and beautiful stories about “taking care of users”, “saving traffic” and other nonsense look very funny. Well, if someone has something to hide, then our task is to bring them to light.
Let's start with the theory. Due to the peculiarities of JavaScript execution, all encryptors and packers, despite their diversity, have only two variants of the algorithm:
Var encrypted="encrypted data"; function decrypt(str) {
} // Execute the decrypted script eval(decrypt(encrypted));
or alternatively:
var encrypted="encrypted data"; function decrypt(str) { // decrypt or unpack function } // Display decrypted data document.write(decrypt(encrypted));
The second method is most often used to protect the source html code of the page, and also by various Trojans to inject malicious code into the page, for example a hidden frame. Both algorithms can be combined, the “sophistication” and complexity of the decryptor can be anything, only the principle itself remains unchanged.
In both cases, it turns out that the eval()
and
document.write()
the fully decrypted data is passed.
How to intercept them? Try replacing eval()
with
alert()
, and in
the MessageBox
you will immediately see the decrypted text.
Some browsers allow you to copy text from MessageBoxes
, but it is better to use this semi-automatic decoder:
For example, let's take some script from Yandex; after looking at the source code, we see something unhealthy:
I’ll say right away that this script is processed by JavaScript Compressor, it is easy to recognize by its signature - the characteristic name of the function at the beginning of the script.
We copy the entire source text of the script, replace the first eval
with
decoder
, paste it into the decoder and save it as an html page.
We open it in any browser and see that the unpacked script immediately appears in the textarea. It’s too early to rejoice, all line breaks and code formatting have been removed. How to deal with this is written in.
Second example. Here is an html page covered with the HTML Protector program. This is a page demonstrating the program's capabilities, so all the options are enabled there: blocking text selection and copying, disabling the right mouse button, protecting pictures, hiding the status bar, encrypting html code, etc. Let's open the source code and take a look. At the very top is the already familiar document.write and an encrypted script. We run it through the decoder, we get a function for decrypting the main content:
hp_ok=true;function hp_d01(s){ ...cut... o=ar.join("")+os;document.write(o)
document.write
in the function with
decoder
and insert after it all three remaining encrypted scripts: For convenience, the scripts are not given in full in the article, you must copy them entirely. We open the decoder in the browser and see the security scripts added by the program and the decrypted source text of the page. For convenience, you can decrypt only the third script, which contains the html code of the page. That's all the protection is. As you can see, nothing complicated. Other protections for HTML pages are removed in the same way.
Let's move on from manual decryption to automatic decryption. To remove the first type of protection, I slightly modified the Beautify Javascript script already known to you and compiled it into an exe file. It handles most JavaScript protections and wrappers I've seen without any problems.
Eval JavaScript Unpacker 1.1
Eval.JavaScript.Unpacker.1.1-PCL.zip (12,073 bytes)
For more difficult cases, you will have to use heavy artillery. This is a free Malzilla project designed to research Trojans and other malicious code. Since all programs designed to protect copyright are clearly malicious, Malzilla will help us in the fight against them. Download the latest version (currently it is 1.2.0), unpack it, and launch it. Open the second Decoder tab, paste the code of the encrypted script into the top window, click the Run script
.
It has fewer functions, but it has a place to be. From the offsite you can download a demo video showing an example of working with the program.
As you can see, there is nothing difficult in removing protection from JavaScript scripts and html pages. Are you still continuing to defend your vile “author rights”? Then we go to you!
Enter text to encrypt:
What is the purpose of the HTML Encryptor tool?
HTML Crypto Tool
"will be useful for webmasters who want to protect their software products from search robots, hackers and those who like to take advantage of the results of other people's work. We are talking about protecting HTML code, which is freely available on most resources and can be easily reproduced by anyone. Using the HTML Encoder tool, you can obfuscate (encrypt, confuse) the source HTML code without any extra effort.
In fact, an encoder can protect everything that is displayed on website pages: texts, images and other web page elements created using the HTML (HyperText Markup Language) programming language. Or CSS codes (Cascading Style Sheets) - special tables in which the code is written once and saved in a separate file.
How it works?
The "html Encryptor" tool allows you to transform the source code of a software product so that its functionality is preserved, and analysis and decryption of the code by third parties or robots becomes almost impossible.
First of all, the page's HTML code and CSS code need protection, that is, those software products that the end user can see on their computer. Of course, you shouldn’t expect 100% code protection from encryption services, but you shouldn’t make life easier for lovers of easy money either. So enter the text to encrypt in the field you see below and click the “Encode” button. As a result, you will receive new text, encrypted via JavaScript, which visitors to your resource and search robots will not be able to read.
Is it worth playing it safe and encrypting everything?
In our opinion, it is necessary to protect not only valuable software products, which are expensive intellectual property, but also simply successful projects into which a lot of effort and time have been invested. It is unlikely that anyone will copy a program written according to a template. But many people will want to use “beautiful” code or copy a successful website design. It is in such cases that our “html encryption tool” will help you. When a user visits your site, he will only see the encrypted code, and “behind the scenes” of the browser, at the same time, javascript will decipher the code and display the resource pages in the proper form.
It is worth noting that this encryption method has its disadvantages. For example, if javascript is disabled in the user's browser, the site will not be displayed. Fortunately, this is quite rare.
This article is an addition to the article about script deobfuscation. Here we will look at the basic principles of encryption and packing, weak points of protection, methods of manual removal, as well as universal tools for automatically removing packers and padded protection from JavaScript scripts. Recently, more and more often, the source code of scripts is encrypted or packaged. Yandex, DLE and other popular projects began to get carried away with this, and beautiful stories about “taking care of users”, “saving traffic” and other nonsense look very funny. Well, if someone has something to hide, then our task is to bring them to light.
Let's start with the theory. Due to the peculiarities of JavaScript execution, all encryptors and packers, despite their diversity, have only two variants of the algorithm: or alternatively: The second method is most often used to protect the source html code of the page, as well as various Trojans to inject malicious code into the page, for example a hidden frame. Both algorithms can be combined, the “sophistication” and complexity of the decryptor can be anything, only the principle itself remains unchanged.
In both cases, it turns out that the eval()
and
document.write()
the fully decrypted data is passed.
How to intercept them? Try replacing eval()
with
alert()
, and in the MessageBox that opens you will immediately see the decrypted text. Some browsers allow you to copy text from MessageBoxes, but it is better to use this semi-automatic decoder:
- JavaScript Decoder title > head >
- // Function for writing decryption results to the log
- function decoder (str) {
- document. getElementById("decoded"). value += str + "\n" ;
- textarea >
- body >
- html >
For example, let's take some script from Yandex; after looking at the source code, we see something unhealthy:
- // Paste the encrypted script here, first
- // replace all calls to eval() and document.write() with decoder().
- hp_ok = true ;function hp_d01 (s ){ …. o = ar. join ("" )+ os; decoder(o);
- hp_d01 (unescape(">QAPKRV%22NCLEWC ....
- hp_d01 (unescape (">QAPKRV%22NCLEWCEG? HctcQa ...
- hp_d01 (unescape (“>`mf{%22`eamnmp? !DDDDDD %22v …
For convenience, the scripts are not given in full in this article; you must copy them in their entirety. We open the decoder in the browser and see the security scripts added by the program and the decrypted source text of the page. For convenience, you can decrypt only the third script, which contains the html code of the page. That's all the protection is. As you can see, nothing complicated. Other protections for HTML pages are removed in the same way.
Let's move on from manual decryption to automatic decryption. To remove the first type of protection, I slightly modified the Beautify Javascript script already known to you and compiled it into an exe file. It handles most JavaScript protections and wrappers I've seen without any problems.
Eval.JavaScript.Unpacker.1.1-PCL.rar (12,124 bytes)
For more difficult cases, you will have to use heavy artillery.
This is a free project designed to research Trojans and other malicious code. Since all programs designed to protect copyright are clearly malicious, Malzilla will help us in the fight against them. Download (currently it is 1.2.0), unpack, launch. Open the second Decoder tab, paste the encrypted script code into the top window, and press the Run script
.
eval_temp
folder contains all the results of executing the eval() functions, including intermediate ones.
They can be viewed by clicking on the Show eval() results
; the text will open in the lower window.
It can be copied, pasted into the top window and immediately formatted by clicking the Format code
. In addition to the decoder, Malzilla has many more tools and settings that make it easy to remove any protection from JavaScript scripts. You can also pay attention to another free tool for working with encrypted scripts - FreShow. It has fewer functions, but it has a place to be. From the offsite you can download a demo video showing an example of working with the program.
As you can see, there is nothing difficult in removing protection from JavaScript scripts and html pages. Are you still continuing to defend your vile “author rights”? Then we go to you!
Ctrl+U
Let's sum it up
Having carried out a rather superficial analysis of the code of the main page of the site, we can draw a conclusion about what tools this page was made with. We saw on it:
- CMS WordPress;
- Google font Source Sans Pro;
- WordPress theme – Sydney;
- Yoast plugins;
- Yandex metrics counter.
Now the principle of analyzing the html code of a website page is quite clear. It is not at all necessary to keep the page you are researching open in the browser. You can save the page code to your computer using the key combinations ctrl+a, ctrl+c, ctrl+v. Paste it into any text editor (preferably Notepad++) and save it with the html extension. This way, you can study it deeper at any time and find more useful information for yourself.
Ctrl+U
How can I view the source code of an element?
Right-click on the page element of interest.
Google Chrome: “View element code”
Opera : “Inspect element”
FireFox : “Analyze element”
In other browsers, look for a menu item with a similar meaning.
Hi all!
I especially laid out the whole point at the beginning of the article, for those who are looking for a quick answer.
The information may be known to many, but since I am writing for novice bloggers, web programmers and other prospectors, this reference article is a must-have.
In the future, you will definitely study the source code of pages and individual elements.
Let's look at a specific example of how you can use viewing the source code of a page.
For example, we want to see what keywords are used for a specific page. We go to the web page we are interested in and press Ctrl+U. The source code of this page will open in a separate window or in a separate tab. Press Ctrl+F to search for a code fragment. In this case, we type the word “ keywords” in the search window.
You will be automatically redirected to a piece of code with this meta tag and the searched word will be highlighted.
By analogy, you can search and study other code fragments.
Viewing the entire source code of a page is in most cases not very convenient, so in all browsers it is possible to view the code of an individual element or fragment.
Let's use a specific example of viewing an element's code. For example, let's see if the link has a nofollow attribute. Right-click on the link that interests us and in the drop-down context menu, left-click on the item “View element code” or similar (depending on your browser). Below, in a special window for code analysis, we get something similar.
We see that the link code contains rel=”nofollow” . This means that PR will not “leak” through this link. We will talk about this in more detail in the following articles. Now the important thing is that you now know how to view the source code of the page and the source code of an individual element.
Stop Continue
Everyone has their own reason for hacking a VKontakte page. This is driven by jealousy, curiosity, anger, resentment, and simply a desire to delve into “dirty laundry.” One of the popular ways to hack VK is to use the script code of the page. It eliminates the use of specialized programs and complex manipulations.
We remove malware or its remnants
If the new profile does not give us access to the page element code and we still see the error, we should do the following:
- Open the Windows command line (“Run”) and enter the “cmd” command there.
- Enter the following command into the line: RD /S /Q “%WinDir%\System32\GroupPolicyUsers”.
- After confirming the action, enter this: RD /S /Q “%WinDir%\System32\GroupPolicy”.
- Now “gpupdate /force” (without quotes).
If everything was done correctly, then after restarting the computer Google Chrome will open the code of the elements and the browser will work normally.
We've released a new book, Social Media Content Marketing: How to Get Inside Your Followers' Heads and Make Them Fall in Love with Your Brand.
The source code of a site is a collection of HTML markup, CSS styles and JavaScript scripts that the browser receives from the web server.
More videos on our channel - learn internet marketing with SEMANTICA
It can be compared to a set of commands given to soldiers by a commander. Imagine that the audience does not see or hear the boss. From their point of view, the military carries out actions independently. In our case, the commander is the browser, the commands are the source code, and the marching soldiers are the final result.
The site is stored on a web server, which sends the page upon user request. A request is typing a URL in the address bar, clicking a link, or clicking a submit button on a form. It doesn’t matter what language the web pages are written in or whether they include a software component. The end result of any server-side algorithm is a set of html tags and text. The page source code is a set of data that includes:
- html markup;
- style sheet or file link;
- programs written in JavaScript or links to files with code.
These three sections are processed by the browser. For the server, this is simply the text that needs to be sent in response to the request.
How to get a code for hacking VK: instructions
To crack the VKontakte code, you need to go to your page, then go to the victim’s page and right-click to copy the source code into a text document. The information obtained will help hack any VKontakte page.
To get your login and password, you need to copy the user ID numbers. After this, all the information will become available to you - his correspondence, photos and much more. You will be able to communicate on his behalf, send spam or advertising.
Important: you need to handle codes correctly and remove unnecessary information in a timely manner, otherwise you can confuse yourself!
It’s not difficult to get codes for hacking a contact, you just need to spend a little time and someone else’s account is in your hands! This method is not a quick hack, but if done correctly, you will take over someone else's data.
Important points
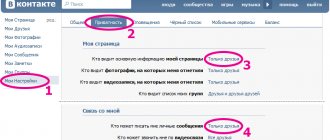
To use the VK function correctly, you need to know several important rules:
- You cannot edit old sent messages.
- You are given only one day after sending to delete and edit.
- Both read and unread messages change.
- The first version of the edited text is stored by email if the profile is configured for alerts.
- You cannot edit other people's messages.
- This function is not yet available in the official VK mobile application.
- The change mark is visible to the interlocutor in the dialogue.
Anyone can get a VKontakte access code, be careful!
Remember, in order to steal someone else’s login information, attackers often send codes that begin with “javascript” and ask them to paste the combination into the search bar and press “Enter.” This is motivated by the fact that in this way you need to confirm that you are not a robot or they are offering a fake opportunity to win a prize. A similar code can be obtained from a friend’s account if it has already been hacked. It is actually a JavaScript mini-program that sends your cookies to the attacker. The program is inserted into links and browsers.
The moral of this story is this: using the “javascript” code you can hack the user, but if such a code comes to you, turn on the best protection in this case - ignoring.
1 vote
Good day, dear readers of my blog. Sometimes you find some beautiful feature on a website and begin to wonder how the creator achieved such an interesting effect.
It turns out that the answer is quite simple. And if you have some skills, you can collect a lot of these features and create your own unique website in a short time.
Today we will talk about how to open the code of a page, a certain element, and learn how to use this skill for your benefit.
Classes and IDs
In the header code we see
Id here is an identifier.
In another case, if you click on the menu, we will see in the code
There is a menu class, that is, the “menu” class is applied to this element.
This is necessary to make it easier to access site elements to change their style. That is, to decide how to change the title element code, you need to find the id - “site-title” and change it to the desired one.
So, all elements of the site code have their own identifiers or classes.
Basic knowledge of code
My site is intended for beginners and first I would like to briefly talk about sites and code in general.
To draw a picture, then cut it into small parts, write code so that the browser will reassemble all the elements into a single whole. Does everything seem very complicated? Not at all, and there’s no point in grieving about it.
This is how high-quality websites are created. If you want, get involved in this matter and study it; if you don’t want to, no one can force you.
I will only say one thing... there is nothing more pleasant than seeing how incomprehensible words you wrote are transformed into a single whole and come to life: links work, buttons move, pictures move, text crawls. I think I know how Victor Frankenstein felt.
When you begin to comprehend the secret language and see that everything is actually much simpler than it initially seemed, you cannot help but believe in your own strengths and capabilities of the brain. This is very cool.
How are websites made? Ideally, first. He's just painting a picture. For example, as shown in the picture below. For now it is just an image, a photograph. No links work, when you click you don’t go anywhere, no search is carried out.
According to this drawing. Look at the screenshot below. You may think that this is a ridiculous and very complex set of symbols. In fact, everything is not so complicated, there is a certain algorithm.
There are only about 150 tags and each of them is responsible for a specific action: link, hyphenation, bold, color, title, and so on. Understanding them is not so difficult if you have the desire and don’t mind the time.
Thanks to knowledge of these attributes, you can solve almost any problem. But each developer finds his own ways to achieve the goal.
Experienced creators immediately see how to achieve results, while others have to think, look for the answer in articles or in the source code of competitors. They simply take the necessary part from a third-party site and edit it for themselves. This significantly shortens the work process.
A little later, I will show you a specific example.
This will be interesting for beginners
Now look how everything works. You find a site and really like some element. For example, this one. You already know how to open the element code.
Now copy it.
I use , paste this code into a new html file, into the body tag (body in English).
Now let's see how it will all look in the browser.
Ready. In order for the text to be aligned to the edges and acquire a greenish color, you need to connect css to this document and copy another code from the site from which we copied this one.
I won't do this now. This requires more time: both mine and yours. I think that I will describe all the details in my future publications. Subscribe to the newsletter and be the first to know when an article appears.
If you can’t stand it, but want to learn more about html and css now, then I can traditionally recommend you free training courses.
Here are 33 lessons that will allow you to master html - “Free course on HTML”
.
And here is complete information about css - “Free course on CSS (45 video lessons!)”
.
Now you know a little more. I wish you success in your endeavors. See you again!
The article will discuss the basic principles of encryption
and
packaging
, weak points of protection, manual removal methods, as well as universal tools for automatically removing packagers and attachment protection from
JavaScript
.
View code
So, let me first show you how to act if you need to find out someone else's html. Then we will look at all the other questions in more detail.
The best way
The method that I will describe first is a little complicated for beginners, but as an introduction, read it. Open the page and click on the right mouse button. Select “Save as...”
Save the entire web page. As you can see in the screenshot, I have already downloaded everything in advance. Here we have two folders.
Everything you need is here. Every element. If you understand this, you can quickly get everything you need. But such a task is increasingly becoming impossible. There is no downloading. What to do if it is prohibited to copy a page?
This is Google Chrome
As you may have already noticed, I most often use Google Chrome and learning someone else's code in this browser is as easy as shelling pears. As in principle with any other. The scheme will not only be similar, but identical. Open the page whose code we want to know and right-click anywhere. In the window that appears, click “View page code”.
A sheet of code will open in a new window, which is quite difficult for a beginner to understand. But don't be alarmed ahead of time.
If you need to know the code of only one element, just hover over it with the mouse and right-click. Select another Chrome function: “View element code”.
For example, I might be interested in how the logo was made, using a picture or a programming language? After all, you can draw a square using CSS. Many experts advise writing down as much information as possible in code. How do they work on popular sites?
Now the necessary information has appeared. html on top, css on bottom. These are two languages. The first is responsible for the text component, and the second for the design. If there were no CSS, then you would have to specify the color and font size each time. For each page, this is very long. But if there were no html, then we would not have texts. I explained it roughly, but in general, that’s how it is.
By the way, if you are interested in how it works here, you can look at the link to the picture below. Here's your answer.
Mozilla Firefox
If you like to work in mastic, then everything will be exactly the same. Open the page and click on the right mouse button. “Page source code” if you want to see the entire code.
When you hover over an element, you can open its code.
Here the data is displayed at the bottom of the screen, but otherwise everything is exactly the same.
Yandex browser
In the Yandex browser, everything is exactly the same as in the previous two options, open the page, right-click, see the page code.
We hover the cursor over an element if we want to find out exactly its code.
Everything is displayed here exactly the same as in Chrome.
Opera
And finally, Opera.
By the way, you may have noticed that you don't have to use a mouse. There is a quick keyboard shortcut to open the code and it is the same for all browsers: CTRL+U
.
For elements: Ctrl+Shift+C.
This is what the result looks like.
Fixing a damaged user profile
To create a new profile, you must delete the old one from your computer. To do this we do the following:
- Close Google Chrome and launch the built-in Windows Explorer browser.
- Enter the following command into the address bar: %LOCALAPPDATA%\Google\Chrome\User Data\.
- When the directory opens, look for the “Default” folder and add “Backup” to its name so that it looks like this: “Backup Default”.
- Now, after restarting the Chrome browser, a new profile will be created.
1) “Social engineer”
Here we must immediately make a reservation that this method is only suitable for those who know little about the Internet, but for some reason decided to register on a social network. As a rule, these are either old people or children.
If you just want to practice, VKontakte beginners can be found here. In this case, one of the laws of psychology applies: a person who does not understand something subconsciously trusts someone who is more experienced in a particular area and takes his words on faith. Here you can create an account for a technical support representative, create an “official” administration email, etc. And create some kind of legend. That new users are required to undergo verification after registration and provide, for example, a link to a certain test, the result or entry of which requires a login pass from VK. The most important thing is that you proceed with caution. The user must be reassured that he is safe. This technique goes well with fake. In addition, advanced social engineers can, having learned the user’s number, call (anonymously, using sip) and send them directly. In addition, all the information you provide (phone number/mention of facts with dates/other) also helps to establish contact with the victim and indirectly indicates that you are from technical support.
2) “Smart” search
A method designed for average users. For this we will need a special dictionary tailored for a specific person. Let's look at the structure of our dictionary:
There is also a VK page on which it is written what passwords should be specified, what characters are possible and the most common passwords. The result was a sheet of 14 lines. But from it we still need to create password combinations that our victim could create. I present to you my small python script that does just that.
From 14 we got 1272 options. I'll give you a part.
Great, now let’s automate the search for passwords through the mobile version of VKontakte with a small script.
Naturally, the example is not optimized. You can also add proxies, multithreading and other goodies, but you’ll do that yourself if you’re interested. But the script itself is capable of entering the missing numbers into VKontakte protection when logging in from another country, and also, using Antigate, it can easily enter Captchas that appear after 5-6 attempts to enter from one IP.