If you don't have
access to the contact e-mail, use the instructions: How to recover your password if you do not have access to the contact e-mail.
If you have forgotten your login or password to enter your Personal Account and you HAVE
access to contact e-mail, follow the instructions below.
If you encounter the error “Access from this IP is denied,” read the information in the instructions: Advanced security settings.
Before the password recovery procedure, make sure that you are registered on the REG.RU website and not with one of our partners (for example, 2domains).
If you have forgotten your Personal Account Login, go through the password recovery procedure. In this case, the login and new password will be sent to the contact email that was specified when registering your Personal Account. Also check: perhaps your Personal Account is set up by email, that is, your email is your Login.
Password – degree of protection, risk of hacking and a pinch of theory
The security that strong passwords provide and the associated risk of hacking are incredibly complex issues. The theory is theory, and great technological progress in recent years has very significantly influenced the likelihood of the capture of confidential data, accounts in online stores or digital identification data of users. A long and complex password provides only superficial security - in the next part of the article we will talk about why.
On the one hand, the computing power of a relatively small computer cluster (a group of interconnected computers for high performance), which has only two dozen video cards, is so great that it can “crack” an eight-character password through simple brute force within a few hours all possible combinations of characters.
Of course, one can imagine the counterargument that increasing the password length will lead to an increase in the time required to guess the password. Although this is a correct assumption, it only works in theory. Some time ago, attackers switched to other methods of cracking passwords. Even shortcut databases, known as symbolic arrays, which collect hash values to reduce password determination time, are slowly becoming a thing of the past.
Self-service center
When none of the described methods are suitable - the phone number has changed, the email has been deleted or is no longer used, and the documents are not saved in the account settings, there is only one method left - contact the self-service center for help. Having found a map of the nearest institutions of this type on the website and going there with a passport, employees will restore access to the office, so that it will again be possible to use government services.
You can also get help restoring access at self-service centers
Password – list of access codes
First of all, due to the numerous cases of mass hacking of accounts on Internet services that have occurred in recent years, there are now a huge number of widely used passwords in the public domain. These intrusions resulted in the theft of millions of customer data. Some access codes were explicitly stored and published on the Internet, while others became the subject of financial transactions.
Having such a password database, it is enough to connect it with multilingual dictionaries to carry out effective attacks. Processing several million words can be done much faster than sequentially searching through a billion possible combinations of characters.
However, this is not the end, because the list of passwords stolen by attackers provides information about the patterns used to create the password. Although simple solutions such as password, 1234... or children's names are no longer used as often as before, incorporating common words and using templates is still the order of the day.
For example, the method of replacing letters according to the pattern used in Leet speak slang is very popular. So, for example, the word kalkulator becomes the slightly more complex k4lkul470r. Some users supplement the passwords created in this way with the name of the portal or service. However, such passwords do not provide an adequate level of security because they have long been included in dictionary files circulating on the Internet.
On the other hand, there are many hardware solutions for which the security leaves much to be desired. For example, earlier versions of Android only lock the screen after five failed code attempts. You can repeat the entry after 30 seconds. If you automate this process, then guessing a four-digit sequence of numbers will take no more than 17 hours.
For a price of 35 euros you can purchase a special device - USB Rubber Ducky, which will perform this task. The protection is fixed only in the latest version of Android (Marshmallow). iOS and Windows Phone are much safer in this regard.
Password for accounts in online services
Above we presented some “behind the scenes” of passwords and methods of attacking security systems. We described methods for creating and remembering strong passwords in a separate article. The question remains of resetting passwords. This operation is often necessary in the case of social media accounts.
In principle, any service, such as an online store, portal, social network or thematic forum, provides the ability to restore access to an account by email address. The system automatically sends a message to the account owner, which contains a special link. By clicking it, the user can set a new password to access the service.
This shows how important mailbox security is. If an attacker manages to obtain the password for their victim's email, they can use the password reset feature to reach all sites registered with that email address. Therefore, it is necessary to take care of the security of your mailbox to a certain extent.
In addition to the password reset function, there are several other solutions for those who forget. These include, in particular, generating a code using the application or receiving a password via SMS message. Google and other major portals even allow you to use security methods such as two-factor authentication. There is also a system for resetting passwords through the correct answer to the “secret” question. Such protection is of little value, since attackers can obtain an answer through social engineering.
Forgot your login and password
Well, lastly, we’ll look at what to do if you don’t remember anything at all, and whether it’s possible to recover your Google account login and password. To do this, at the very first login step, select “Forgot your email address.” mail?
Next, try entering your number, provided that you have not changed it for a long time and it was recorded in your profile as a backup. Also try to indicate all the mailbox addresses that you have (one by one, of course). Perhaps one of them is listed in your profile as a backup. Click "Next".
If you guess correctly, you will receive a message by email or phone with a code. Enter it and change the password.
Remember what first and last name were indicated. They could be real, it could be a nickname - try all possible options. Please note that every letter has a meaning here. For example, Olya and Olga are different options.
If you remember, you will gain access again; if not, a message will appear: “This Google account does not exist.”
If you tried everything and nothing worked, you can use our instructions and create a new Google account from your phone or PC.
And this is where I will end. Follow the instructions strictly and answer the questions as correctly as possible and you will be able to recover your Google account password in a couple of steps. When you go to your profile, I recommend that you immediately indicate a backup phone number and email - this is so that in the next similar situation, everything will go easier and faster. Also be sure to write down your password in a safe place.
Access to a Windows computer
Don't panic if you suddenly forget your Windows account password. You can gain access to the system without using password cracking tools. The whole operation is somewhat risky, but only takes a few tens of minutes. Even works on Windows 10.
Restoring access to Windows without an installation disk
When the login screen appears, turn off the computer by pressing the switch on the back of the computer or unplugging it from the electrical outlet.
Attention! The editors are not responsible for possible damage to the computer. Although this happens rarely.
the Start Windows normally button, select Run Startup Repair Tool (recommended) . Wait while the system sorts out the data loading. Windows will ask if you want to restore your system using the recovery feature. Click Cancel. The system will begin actions to eliminate them. After a few minutes, a Show problem details list box will appear at the bottom of the screen. Expand it and scroll to the very bottom.
Click on the link X:/windows/system32/ru-RU/erofflps.txt to open a text editor. In the editor window, select the menu File → Open and go to the /windows/system32 directory on the system partition C:
In the lower right corner there is a drop-down list with the default option Text documents (*.txt) selected. Select All files (*.*) in it. Select the Utilman.exe file, right-click it, and select Rename. Temporarily change the file name to, for example, Utilman1.exe. Similarly, replace the file name Cmd.exe with Utilman.exe. Click Cancel, then close the editor window and system recovery tools.
After you confirm the action with the Close button, the system will restart. The login screen will appear on the screen. Click then the Accessibility icon in the lower right corner. A command prompt window will appear. Type net user [name_user] * , replacing the variable [name_user] with your own name.
The system will ask you to enter and repeat a new password. Press Enter. Close the text console window. You can now log in without entering a password. Remember, however, that you must assign a new password to your account.
Using old password
Open the Chrome browser (or the one you usually use) on your computer and on the main Google search page, click the “Login” button to log in to your account.
Then enter your login - this is either a phone number or email address. Click "Next".
It’s at the next step that the problem arises. Here you need to click “Forgot your password?” to reset it.
If you recently changed this combination to another, then simply enter the old set of characters in the field provided and click the “Next” button. This method is relevant if you changed it not so long ago - you haven’t remembered the new one yet, but you still remember the old one.
Now the system must verify that it is really you. A notification will be sent to your device. If you didn’t receive anything, or you clicked the wrong button, select “Send again.”
In the notification sent, click the “Yes” button.
The old password will be reset and a window will appear where you need to enter a new set of characters and confirm it. Then click “Change”. Now you can go to your profile.
Password – access for mobile devices
When you lose access to your account on your mobile device, it is not at all necessary to reset it and lose all your data. With access to your Google account, you can use the app to unlock your lock screen, just like you can with other apps.
A free application for Android smartphones is [Free] Screen UnLock/Lock. A commercial application, Screen Lock Bypass Pro, is also available. Both applications are very easy to use. A little more effort is required to remove the block using Android Debug Bridge.
Users of a locked iPhone have at their disposal only the methods proposed by the manufacturer. Apart from them, there are no tricks that would help remove the screen lock. But at least you can restore your device from a previously created iTunes backup, so you don't have to set everything up again, as is the case when using Safe Mode.
Windows Phone smartphones can be reset remotely and even their contents can be deleted. Alternatively, you can get a similar effect by pressing a specific key sequence. One way or another, you will have to come to terms with the loss of all data in the smartphone’s memory.
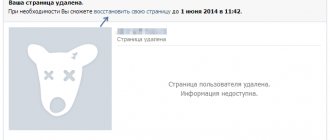
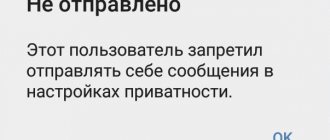
What to do if there are photos on the page, but VK writes that there are none?
An example of an error: “There are no photographs on the page that can be used to identify its real owner. Therefore, unfortunately, access to the page cannot be restored."
This happens not only when there is not a single photo on the page. If the photo is only in saved ones, on the wall or in other albums, but there is no photo with a face among the avatars (the “Photos from Page” album), the error will be the same. Other possible reasons are that there is not a sufficiently high-quality photograph of the face or there are other people in the photograph.
If you think that an error has occurred and there is still a suitable photo with a face on the page, then you can send a request to VK agents. More details here:
- How to restore a VKontakte page if there is no photo on it