The VKontakte social network is the largest in Europe and the seventh largest in the world by the number of users. As of 2021, 410 million people are registered on the site. It is inevitable that such a large site could potentially become a breeding ground for scammers and criminals. Despite this, there are no fewer people wanting to register, and more and more people wanting to hide their personal data every day. And the reasons for such “conspiracy” can be very different. The vast majority of users take part in various discussions and groups, comment on photos and videos, share their own emotions and impressions, and are active. But it is possible that the user will want to abstract himself from prying eyes. The site administration took into account the likelihood of such a desire among users and included the appropriate settings in the site functionality. If you do not want to advertise your personal information, in this article you can find out how to hide your VKontakte page.
Where are the settings in the new VKontakte design?
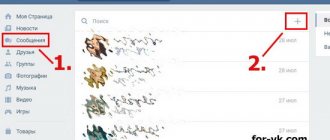
The settings in the new design are located in the upper right corner of the page, next to a small photo of the user and his name. To open them, you need to click on this circle - a pop-up menu will appear, where you should select “Settings” .
There you can edit the general appearance of the page, hide the sections that are displayed, change data, enable or disable notifications for comments and likes, configure which sections are visible to other users and friends, and, if desired, hide what you do not want others to see.
In the mobile version of the site, the settings section is located at the bottom of the main menu of the page: under the “News”, “Photos”, “Applications”, etc. tabs.
How to close a page from external users
To hide a page from external users, you need to go to the “Settings” section, select the “Privacy” tab, scroll down the page and find the column “Who can see my page on the Internet.” There you can choose from three options:
- absolutely everyone, including search engines (this means that if someone enters a search query in the browser, they may come across your page among the results found, and the person will calmly follow this link);
- everyone except search engines (this means that if you leave a link to your page somewhere, anyone can click on it and see your profile, but your page will no longer appear when searching the Internet);
- only for those who have their own VKontakte page (if a person does not have his own page or is not currently authorized, then he will not be able to view your profile).
From this list you need to select the item you need. Usually the default is “page visible to everyone,” but it is recommended to specify “only site users.”
Methods of hiding information
Information on a hard drive can be hidden using several methods. We will talk about them, starting with simple ones and moving on to complex ones. An article for those who hide and don’t find. Therefore, the methods of concealment are only indicated. Anyone who needs more detailed information on a particular method will find it and, most importantly, add their own unique flavor by mixing seasonings. And specific recipes would be useful to those who search and not hide.
#1. Moving to “away” folders
The method is to move the information somewhere in C:\Users\Walter\AppData\Local\Temp\018iasywq8\user\10ha1pg1vythz21ds778b0ycq9r2. This method is used by... well, those who, in principle, know that the computer operates from the network and is turned on using a button. How can I find it? Well, since videos and images are usually hidden there, then search through Total Commander: *.jpg; *.avi or *.doc; *.xls and so on.
#2. Hiding in the archive
The method is clear. Archive 10 photos, name the archive hjskdhklgd.zip and combine with method No. 1. There should already be a user who has an idea of what an archiver is. How can I find it? Just like in the first paragraph, just indicate “search in archives”.
#3. Renaming a file
Light
. Although the method is simple at first glance, with in-depth use it can give some results. Depends on how experienced the user is. If his knowledge is limited to the level described above, then the file "my_black_accounting.doc" will be named "communism_builder_code.doc". You can find it the same way as above.
Medium
. If a person knows how to include file extensions or is friends with TK or FAR, and also understands that when renaming a file does not lose its taste, then he can rename it, for example, to intraweb.dat, combining with the first + second method and get some effect. You can only find it by running a search on the initial characters of the file contents to identify the desired type. *.* search for the text “II*” this is tiff and so on.
#4. Applying attributes
The method is also clear. Right mouse button, “hidden” attribute. At the command line attrib –s –h. A very common piece of advice when searching Google for “Hide files”. I don't know who it's intended for. Find? Guess it 3 times, it's called.
#5. Renaming a folder
Light
. One of the funniest methods, but with its vivid visual effect it impresses many. It is recommended to rename the folder on the desktop to 255 while pressing ALT. In this case, the folder name will be empty. And change the folder icon to an empty picture. And as if by magic, the folder becomes visually invisible. Find? Hold down the mouse button to select the entire desktop area.
Medium
. There are also users who assign the folder the system name. It then takes the form of Fonts.{21EC2020-3AEA-1069-A2DD-08002B30309D}, for example, the control panel and with the 2nd click it actually leads there. You can find it by knowing that ordinary people do not have a link to the control panel in the “My Documents” folder. Well, methods 1-2, of course.
#6. Encrypted archive
Now we are not talking about how to view information, but about how to find it. Therefore, encryption itself and passwords are not discussed. The fact is that modern archivers have the ability to hide the names of files in the archive during encryption. Here we have already come to something interesting. The user at least spent several hours learning about this method and understanding it.
Find? You can only find the archive itself, and determine that it is encrypted in such a difficult way. The files in it are never visible. That is, the fact of hiding information on the computer will be revealed. This is already enough for this article.
#7. Installing special programs
The methods of programs for hiding information are the same as written above or, basically, below. But the very existence of such a program already indicates the fact of concealment of information. And, of course, after uninstalling it, all the files are in full view. This method is useful for those who have curious people on their computer. Typically, such programs are password-protected, so it is so easy not to uninstall them, including when gaining access to a computer over a network.
But... all existing programs designed for the average user reveal the fact that information is being hidden, and attract more attention than such information itself. They put huge red signs on folders, run in autorun and tray, and have stupid names like “My hidden files.”
One of the most famous vendors in this area, Symantec, makes a folder with a huge sign NORTNON PROTECTED!!! Imagine a situation where some criminals decided to hide a stolen two-cassette tape recorder in their home before a search. They go to the store, take a passport (this is how they buy programs abroad) and buy an expensive super safe. They put it in the middle of their apartment and put a two-cassette player there. The servicemen come, go around the whole house, there is no double-cassette player. Naturally, they ask: “What is this safe in the middle of the apartment?” And they said to them: “It’s none of your business! This is our Private property!” Well, of course, fingers are in the doorway and the safe is open... So the only thing worse than such programs can be placing all the secret information on the desktop with the inscription: “My secret files are stored here!!!”
#8. Virtual disks
The method is very common and... very ineffective. True Crypt, for example, creates an encrypted file hundreds of megabytes in size and then mounts it as a disk. Moreover, all information, and not just the files needed at the moment, is visible both over the network and when receiving secret surveillance. And most importantly, if it is necessary to hide the very fact of hiding information, then this is the most primitive way. Finding a file of, say, 700 MB in size, which is encrypted, is not at all difficult.
#9. Hiding logical drives
The method is not bad, considering that there are no large files and you won’t find information by searching. The idea is that Windows gives you the ability to connect and disconnect drives. If a disk is disconnected, then it is invisible... until any disk editor starts. And this, of course, is not so difficult. And again, during work, all information is revealed. And it is visible both over the network and during a remote attack. The downside is that splitting an existing disk on the go is unsafe. That is, it is better to take this point into account when formatting.
#10. Steganography
You can take shorthand either manually or using special tools. Information is usually hidden in graphic and video files. Where you can trim the color scheme and you won’t be able to see the difference by eye. Starting from this point, I will not write how hidden information can be found, I will only talk about what level of specialist is needed to detect it.
If it is unknown what tool was used to hide the information and in which file it was hidden, then I would rate the level of the discovery specialist as quite high. We’ll talk separately about the categories of people who can find hidden information below.
#eleven. NTFS Data Streams (ADS)
NTFS allows you to attach as many data streams as you like to one file. Such data is not visible to the naked eye; neither connecting another OS, nor safe mode, nor viewing with DOS will help. On the one hand, it’s not so difficult to detect, but... only for a specialist. A non-specialist will not find such information.
On the other hand, the method is not particularly common. If you consider that the information can be attached to the service data of NTFS itself, then the search in general can be greatly complicated. If you combine other methods with ADS, the task becomes simply complicated. A high and mid-level specialist will be required, depending on the combination of different methods with ADS.
#12. Hijacking native Windows functions
Despite the fact that many programs use this method, it is presented so stupidly that all the charm is lost. But this is real freedom, there are no boundaries, Windows turns into an obedient ball of plasticine. It no longer depends on the will of old man Gates, everything becomes in our hands.
The idea is to intercept operating system requests to the disk and return values with a filter. Even though Windows tries its best to show the file "topsecret.doc", the hook used makes it think that the file does not exist. The big downside is that if we remove our hook, Windows will work correctly again. Of course, when you start creating, you can’t really do things like “demolish a hook” either, combining this method with other high-level methods.
#13. Games with MFT
There is such a bad file on NTFS, called MFT. So, he carefully logs all our writes to the disk. It’s not difficult to guess what you can do if you know how to rein him in with such zeal. Here are object indexes, uplinks, substitution, and so on. But, from this point on, there are no tools for this kind of magic. There must be brains here. But the difference in taste is like between catering and an expensive restaurant.
#14. Intervertebral herniation (IGH)
There are spaces between files that are formed due to the fact that the file weighs 500 bytes and the sector size is 4 KB. So this file occupies the entire sector. And then who will occupy the free space? Few people can put information there, and you should completely forget about special tools. But the effect! And, of course, to suspect that the computer under study has an MPG?! Therefore, specialists of the highest class are needed.
#15. Removal
It is interesting that this simple procedure is at the highest level with us. Yes, by deleting the file, you hid it, and very securely. I will not dwell here for a long time on the fact that only a blast furnace deletes information from a hard drive. And I’m not talking about banal deleting to the trash (by the way, there are users who hide files in RECYCLE). I'm talking about average file deletion. When Windows and its applications never find the information. Of course, another question is how to work with such information. Here you need to know a lot, be able to do a lot. And, to be honest, there is more theory here, but... I’ll give this art pride of place No. 15.
Who can find hidden information
Speaking about this, those who like to show off their erudition and impress others pronounce the mystical phrase “special services.” Some, especially those close to them, give out the abbreviations NSA, and some even know the decoding (National Security Agency), SVR, FSB, GRU, etc.
I always find it funny for 2 reasons. It is the special services that exist in 5-6 cities around the world that will not be interested in the information and persona of ordinary users. Therefore, we will modestly remain silent about these services, their capabilities and methods.
In reality, information is hidden from “merchants” in uniform who confiscate the PC during the next “action”. In order to pay the standard amount, and not also pay for some secrets that may be discovered, you can hide information. Or if unlicensed software is hidden from the same category of “employees”. “Businessmen” usually do not have very deep knowledge in this area, so methods 2+ can be considered sufficient in this case.
You can hide the personal, purely intimate part of your life simply from everyone. If they are home, then almost all methods will do, unless, of course, one of the home is a representative of that same NSA. If at work where there is an admin, then the situation is complicated by the fact that usually there are no admin rights, which are needed for simpler methods. So, of the simple ones, 6 and 8 remain (for example, if TrueCrypt is configured to work without admin rights). And out of real ones, 10, 11. But, of course, keeping such information at work is stupid. Moreover, more and more organizations are secretly monitoring employee computers using many different utilities, such as ActualSpy. And then the meaning of concealment is completely lost.
But these are all routine and banal things. Real specialists do not work in the special services, but in Gazprom, Nokia, Adobe, Oriflame, etc. The real value is the information where there is a super competitive multi-billion dollar environment. Such companies spend a significant portion of their budget on competitive intelligence and counterintelligence, and their specialists, methods and technologies are several years ahead of the Pentagon and MOSSAD. For such specialists, the methods described above are only a matter of short time.
Conclusion
The conclusion is very simple and unambiguous: no known methods of hiding information can prevent its detection. So, if information needs 100% protection, it must be encrypted. However, if the information is securely encrypted and not hidden, then I recommend studying the chapter “Interrogation” of the immortal work of A.I. Solzhenitsyn’s “GULAG Archipelago” and it will immediately become clear to you that no one will engage in cryptanalysis if we live in a country with such “glorious” traditions of the Cheka.
How to close a VKontakte page from those who are not friends
In early versions of the site, you could completely hide your page from those who are not on your friends list: outsiders saw only your photo and username, and the rest of the information was hidden. To gain access, you had to submit a friend request and wait for it to be approved.
In the latest versions of the site, it is impossible to close the page as it was before. The new design also did not bring back this option. The only way to close a page is to add users to the blacklist. If a person does not want someone specific to come to him, then this will help, but it will not be possible to block absolutely everyone.
Another option is to close all sections from those who are not on your friends list, including personal information, but in this case the profile photo and wall posts will be visible to everyone. This can be done in the settings in the “Privacy” tab in the first section “My Page”, as well as in the next “Wall Posts”. You can only hide photo albums and videos manually.
What can be hidden on VKontakte
The developers took the issue of privacy settings very seriously. Using standard privacy options, you can hide almost any part of your profile. The settings are so flexible that, if desired, you can even hide one or more comrades. They will remain your friends, but no one will be able to see them on the list.
It is also possible to hide certain information from specific people whom you do not want to involve in your affairs. For example, in the settings you can limit users who see the list of gifts by selecting one of the following settings options:
- All users. Anyone registered on the VKontakte social network can see who gave you a gift.
- Only friends. All people with whom you agreed to be friends in VK will see a list of gifts.
- Friends and friends of friends. Each person you are friends with, as well as their comrades, can view the gifts they have received.
- Everything except... With this setting, you will allow everyone to view information, with the exception of some people whom you can choose yourself.
- Some friends. This option is the complete opposite of the previous one. By selecting it, you will prevent everyone except a few trusted users from seeing your gifts.
- Just me. This is the choice of the most secretive users. No one on the Internet except you will be able to see the list of gifts.
We recommend: How to log out of VK on all devices
You can view the list of elements whose privacy can be adjusted in the settings of your page. At the moment, the list of options contains 27 items.
How to hide sections with music, videos and photos in the new design
In the new design, only audio recordings can be hidden from strangers at once, and photo albums (except for profile photos) and videos can only be removed manually. For audio recordings, you need to go to the page settings and the “Privacy” tab. There will be a separate column “Who can see the list of my audio recordings”, in which you must select the one you need from the proposed options.
For photo:
- go to the “My Photos” section;
- select the desired album;
- hover over it;
- in the buttons that appear, select the pen icon, i.e. editing mode;
- click on “who can see the album” and select the one you want;
- don't forget to save the settings.
The same applies to video recordings, but you will have to edit each video separately. You can hide “Videos of me” and “Photos of me” in your profile settings.
How to restrict access to your page
You can block access to your entire page or part of the information on it using the instructions below.
- Go to your account settings page. You can get to it through a pop-up menu by clicking on the avatar icon.
- In the right menu, select the privacy settings column.
- You will see the entire list of elements, the degree of accessibility of which can be adjusted. To make it easier to navigate, the entire page is divided into 5 blocks: My page.
- Entry on the page.
- Contact me.
- Stories.
- Other.
Using the instructions and recommendations provided, you can easily deny or, conversely, allow access to one or all users at once to the page and its parts. Don’t forget to help your friends understand the intricacies of the VKontakte social network - share this and other articles from the site vkbaron.com with them.
How to hide posts on a wall
The only thing that definitely cannot be hidden from strangers on the VKontakte website is profile photos (“avatars”) and posts on the wall. The page owner can only limit the ability of outsiders to comment on posts , which is done in the page settings in the “Privacy” section. There is another option, but it will only affect future entries.
There is a lock icon in the post publishing window. If you click it before publishing a post, it will only be visible to users on your friends list. But this doesn't work with reposts from other people's pages, and old posts will still be visible to everyone unless they are deleted.
So, the new design of the VKontakte website has moved the section with page settings to the upper right corner. By selecting “Settings” and then the “Privacy” tab, you can limit access to your page and certain sections. But some manipulations will have to be done manually later: for example, this way you can hide photos and videos.
To check what the page looks like for different groups of users or different people from the friends list, you can use the same “Privacy” page: if you scroll to the end, there will be a link at the very bottom, clicking on which the user will switch to viewing mode. By selecting different people, he can see what parents, close friends, or users whom the person does not know and who are not on his friends list see on the page.
Privacy settings process to hide a page
To create hidden VK pages, you don’t need complex actions; everything is done very simply.
In the upper right corner, click on the thumbnail of your avatar. In the window that opens, click on the “ PRIVACY ” item.
From your computer, you can get to the privacy settings section by following the link - vk.com/settings?act=privacy
Here you will find a lot of things that may be useful to you.
- Completely stop contacting all users of the site. To do this, you need to select the answer “no one” in each item in the “contact me” section. (See Close messages in VK).
- Almost completely, hide all information and all content on your page from others. To do this, in each item in the “my page” section, select the answer “only me.”
- Prohibit anyone who is not registered on VKontakte from viewing your page. To do this, in the “other” section, in the “who can see my page on the Internet” item, select the answer “only to VKontakte users.”
- Hide up to 30 people from your friends and subscriptions list. To do this, in the “my page” section, in the “who is visible in the list of my friends and subscriptions” section, click on “all friends” and select names.
- Hide a friend's page. To do this, in the “my page” section, in the “who sees my hidden friends” section, select the category you need.
- Hide interesting pages. To do this, in the “my page” section, in the “who sees the list of my groups” item, select the item you need.
Please review the item and answer option thoroughly before changing the setting.
Here, in the privacy settings, you can limit the list of users who can view the basic information of your page, your photos, audio and video, and your posts. You can limit the list of people who can post or see posts on your page. If you need to reopen audio recordings (See How to open audio recordings in VK).
At the very bottom of the page you will find the “See how other users see your page” function, which will allow you to make sure that the settings you have made are correct.
Details in privacy settings
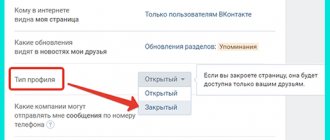
If you want to hide the page completely and from everyone, then, unfortunately, the site does not have such a function.
If you use everything that is available in the privacy settings, some items will still be available for viewing by other users, namely:
- Avatar photo;
- Date of birth, language, country (if specified);
- Your wall (except for posts of other users);
- Contents of the photo albums “photos on my wall” and “photos from my page”.
If you do not want to share even this information, you may well leave incorrect information about yourself and fill out only the required fields when registering. You don't have to post a personal photo of yourself on your avatar, and you shouldn't post on your wall if you don't want to share it with other users.
You can hide a VKontakte page, entirely, only from individuals.
That is, you must specify each user whose access you want to deny individually. The number of such “blockings” is not limited.
You can block access to your page by clicking on the small square button under the user’s avatar and selecting “block user”.
If the user you are blocking is your “friend,” then first you need to unfriend him.
You should know that if in your privacy settings you select the answer “no one” or “just me” in each item, and no activity on your part is recorded for a three-month period, your account may be deleted from the resource by the administration.