Who needs this kind of cheating and why?
Boosting messages through page element code is a very simple method that is not suitable for all users. Its main feature is that you can generate an infinite number of drugs instantly, but they will not be saved when you update or close the browser tab.
When I say “infinite,” I mean precisely an infinite number, limited only by the interface of the VK site itself. That is, how many numbers opposite the “Messages” line the interface can accommodate, that’s the number you can wind up.
But as good as this method is on the one hand, it is just as bad on the other. All changes will not be saved, but will be available only until the end of the current session. That is, using the page element code, you will earn, say, 10 thousand hp, and then close the site. When you open it again, there will be no changes.
The thing is that by changing the site code, you do not send information to the VKontakte servers. You only visually change the element in the browser itself. This information does not go anywhere beyond the browser and, accordingly, is not stored anywhere.
The method of boosting messages in VK through an element code is suitable in cases where you need to take, for example, a screenshot on which a large number of DMs should be visible. They cheated it, took a screenshot of the screen, and sent it to a friend or to their envious people.
Idea!
Where did it all start? And since I, being a lover of the English language, found the LinguaMania application on VKontakte. This is a language learning simulator. To make learning more fun, the developers have implemented a reward system in the form of letters, from which you can collect words, and then “buy” clothes for them and wear your virtual avatar. And, of course, the rating. Here's more about it. The rating is given not only for learning using virtual “textbooks”, but also for playing a quiz, which immediately interested me.
This is what the gameplay looks like
For the first few weeks, I honestly scored thousands of points until I got tired of it. Having scored 100,000 points and being 2-3 times ahead of my pursuers, I was pretty tired and gave up on this matter. But after several months they began to catch up with me in the rankings. It was then that my egocentrism woke up: the desire to maintain the first line of the ranking forced me to think about ways to gain points without wasting time.
The first thing I did was look at the application traffic: what was being sent where, what was coming back. I have never seen a better tool for analyzing HTTP traffic than the HTTPWatch application for Internet Explorer. So, I launched the game, clicked the “Record” button in the add-on to record logs... and here, as they say, “2 aces came preflop”. I saw that the application transmits all its data as is, in the open.
Traffic through the eyes of HttpWatch
Having studied the traffic, I discovered that the state variable takes the following values: PHASE1, PHASE2, PHASE3, GUESS, LOSE. This corresponds to the stages of the game in each round: all letters are hidden, one letter is revealed, two letters are revealed, the word is guessed, the word is not guessed. As you can see, question_id is transmitted openly, which, as you might guess, is the question number. In the case of the first three phases, the word mask is transmitted in the “question_mask” field. For example, if state=PHASE3, the first letter is C, the second letter is A, then the word mask is ??C?A. If the current phase is GUESS or LOSE, the entire word will be displayed on the screen to show the user the answer. Accordingly, this will also be displayed in the question_mask variable: the word in full will be there, without question marks.
Watch attentively. At the end of each round we receive a question number and the answer to it. It was this discovery that gave me the idea to automate the process. After all, every time we receive a word, we enter it into our word database. If such a question_id is already there, then we take the word and enter it into the program window, for which we receive points. It goes without saying that checking for the presence of a word in the database should be done at the moment when the state is PHASE1, PHASE2 or PHASE3. Thus, our bot will be self-learning: there is no word - we remember, there is a word - we answer the question.
How to wind it up?
When using this cheating method, it is important to understand that in fact no messages will be sent to you. You just change the number opposite the corresponding main menu item.
In other words, all your popularity gained in this way remains only in the screenshot.
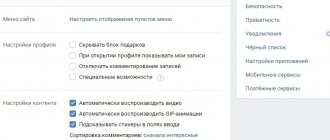
Below I will describe step-by-step instructions on how to generate messages in VK using the element code:
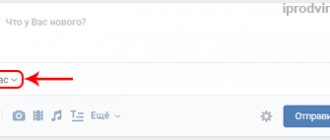
- You must receive at least one incoming message for the number “1” to appear opposite the “Messages” line.
To do this, ask your friend to send you a PM or do it yourself from another account. The main thing is not to read it.
- Next, click on this number with the second mouse button.
- Select Explore Element or View Code. This item is called differently in different browsers. By default, everywhere this is the keyboard shortcut Ctrl+Shift+I.
- Afterwards, a window will open on the right with the page code expanded in the place where the selected element is registered.
If you can't find the element you need in the code, then simply hover your mouse over each of the lines. At this moment, the selected elements will be highlighted on the page itself. Find the line that, hovering over it, highlights the “Messages” line. Unfold it.
- Find line 1
The number “1” in this line is responsible for the displayed value of the new drugs.
- Change it to the desired value, for example, 99999.
- Press the key
Voila! You can see the result in the screenshot.
Everything is much simpler than it might seem at first glance. If you look at it, this procedure is very simple, and it can be carried out at any time in half a minute. Now all you have to do is take a screenshot and brag to your friends.
Coding
How can all this be implemented in practice? First you need to learn how to intercept traffic yourself. Let's look at the options available to us. There will be three of them.
The first option is to intercept network interface packets. A fairly low-level method that requires skills in interacting with external libraries, network interfaces and, in general, the ability to work with the operating system at a low level. You will find the WinPCap library useful, which allows you to receive packets in their pure form directly from the network interface. For the rest - Google to the rescue.
The second way is to work with Internet Explorer. This method is perhaps the highest level, since we receive ready-made, processed traffic. To intercept traffic in this way, you need to know COM programming: be able to connect to COM objects (which is the IWebBrowser2 component inside the Internet Explorer window), implement interfaces and work with them. The method requires serious knowledge in the above area, so I decided to do it “as my grandfather taught,” the third way. And this is our implementation of a proxy server. More precisely, Socks 4/5 servers. Let us focus our attention on this method. Let’s sharpen things up a bit, since this article is not about creating a Socks server, so I won’t load it with code.
You should start writing a Socks server by studying this manual. For the lazy and English-speaking, my explanations will be in Russian. But first, let's implement the server application. There are several ways to make a server application, starting with the old...
SOCKET mysocket sockaddr_in local_addr; local_addr.sin_family = AF_INET; local_addr.sin_port = htons(MY_PORT); local_addr.sin_addr.s_addr = 0;
mysocket = socket(AF_INET, SOCK_STREAM, 0); bind(mysocket, (sockaddr *)&local_addr, sizeof(local_addr)); listen(mysocket, 1080);
SOCKET client_socket; sockaddr_in client_addr; int client_addr_size = sizeof(client_addr);
while ((client_socket = accept(mysocket, (sockaddr *)&client_addr, &client_addr_size))) { DWORD thID; CreateThread(NULL, NULL, ClientThread, &client_socket, NULL, &thID); }
...and ending with a completely modern way of implementing servers under Windows, which is working with network messages using the WSAAsyncSelect() function. The program itself and its complete source code in C++ in the Visual Studio 10 environment can be found on our DVD. The scope of the article does not allow me to describe in detail the process of creating a Socks server, so I will limit myself to only explaining the structure of the program and the main methods that I used.
You should start writing such an application with approximately the following code:
SOCKET server_socket; WSADATA wsaData; int server_port = 3128; int queue_size = 5; struct sockaddr_in server_address; #define SERVER_ACCEPT WM_USER + 1 #define CLIENT_EVENT WM_USER + 2 #define TARGET_EVENT WM_USER + 3 #define SOCKET_OPENED WM_USER + 4 #define SOCKET_CLOSED WM_USER + 5 int ServerStart(HWND hWnd) { int rc; WSACleanup(); WSAStartup(0x0101, &wsaData); server_socket = socket(AF_INET, SOCK_STREAM, 0);
server_address.sin_family = AF_INET; server_address.sin_addr.S_un.S_addr = inet_addr("127.0.0.1"); server_address.sin_port = htons(server_port);
bind(server_socket, (LPSOCKADDR)&server_address, sizeof(server_address)) ; listen(server_socket, queue_size); /* !!! */ rc = WSAAsyncSelect(server_socket, hWnd, SERVER_ACCEPT, FD_ACCEPT); return 0; }
How does this code differ from the first? And the fact that in this case we do not need to bother with multithreading to process each connection to the server. Thanks to the highlighted line, we will receive SERVER_ACCEPT messages in our hWnd window every time a new client connects.
Now let's look at the moment of connection. In the window's message processing procedure, we catch the SERVER_ACCEPT message and work with it. As soon as the client has connected, the accept() function is called, and then the CLIENT_EVENT event is registered, which will be sent to the main window of our program as soon as data or a message about its closing arrives on the socket:
client_socket = accept(server_socket, (LPSOCKADDR)&socket_record->client_address, &len); rc = WSAAsyncSelect(socket_record->client_socket, hWnd, CLIENT_EVENT, FD_READ | FD_CLOSE);
Let's return again to our window procedure. In it we will process the above-mentioned CLIENT_EVENT event. The value of lParam in this case will be either FD_READ (if the event was called as a signal about the arrival of data on the socket) or FD_CLOSE (if the socket was closed).
if(WSAGETSELECTEVENT(lParam) == FD_READ) { c = recv(socket_record->client_socket, &bf[0], 1,0); ... } if(WSAGETSELECTEVENT(lParam) == FD_CLOSE) { ... }
Thus, we have already learned how to accept connections and read data from the socket. But let's return to the implementation of the Socks protocol mentioned above. Here I will show how Socks5 works, although version 4 is also implemented in my program. That's what the RFC tells us.
After connecting, the client sends two bytes to the Socks server: the version number (4 or 5) and the number of authentication methods: N. After that, we will receive another N bytes with the numbers of these same methods. Usually 3 integers come: 05h, 01h and 00h. That is, the fifth version and the first method, the value of which is 00h, meaning that the client wants to work without authentication. In response, we must return two bytes. The first is the version number, that is, 05h, the second is the value of the authentication method we (the server) selected from the list that the client offered us. Since the client usually only offers 00f, this is what we will return. Having eaten our response, the client will send a request in the following format: the first byte is the version number, the second is the command, the third is the reserve byte, the fourth is the address type. After which there will be a group of bytes directly with the address of the target host itself, and the packet will end with two bytes with the port number of the target host. The format of the target host address group of bytes will depend on what type of address (the fourth byte) is specified. We will work with the usual IPv4, which corresponds to the value 01h for the fourth byte of the request. In this case, the group of bytes will be size 4, which is the standard IP address format of four integers. The target host port number is calculated as first byte * 256 + second byte.
So we have a request from the client that needs to be fulfilled. We connect to the target host using the address and port given to us, and wait for data. We will wait for data both from our client’s socket and from the newly created socket for the target host, with which the client wants to communicate through our Socks server. We send everything that comes from the client to the target host. Everything from the target host goes to the client. This is how the Socks server works.
My program implements a structure containing data about all the connections we have created, so that when we receive an FD_READ message, we know which socket is sending what and where, whether it is a client or a host target, and what the status of the communication process with it is. The scope of the article does not allow a detailed description of this structure, so see the source code.
So, we have learned to redirect traffic and therefore listen to it. Now, I think it won’t be difficult for you to write parsing the necessary data. When processing the data, we, as I indicated earlier, look to see if there are records in our database for the desired id. If not, then at the time of the LOSE or GUESS phase we enter this word into the database. If there is a recording, then it’s time to tell the game the correct answer. This can be done in two ways.
The first is “very high-level” and at the same time complex. It consists in the fact that we connect to the IWebBrowser2 COM object inside Internet Explorer, in which we have the game loaded. We get the Flash movie interface and work directly with it via the Flash API, which will allow us to enter the word directly into the text field and press the enter button. This is very cool. And very difficult :).
What if you don't use Internet Explorer? And you don’t have enough strength and desire to implement all of the above? There is a good old method of emulating mouse and keyboard events. It consists in using the SendInput system function. This is an upgraded version of keydb_event()/mouse_event(), which is recommended by the manufacturer (Microsoft). Here is an example of pressing the F5 key:
INPUT pInput; pInput.type = INPUT_KEYBOARD; pInput.ki.wVk = VK_F5; pInput.ki.time = 0; pInput.ki.wScan = 0; pInput.ki.dwFlags = KEYEVENTF_EXTENDEDKEY; SendInput(1, &pInput, sizeof(pInput));
Hooray! Now we can listen to traffic through our Socks server, educate ourselves, expanding our vocabulary with each new word, and answer questions that we have already encountered. Goal achieved!
It is worth adding that the program posted at the link above does not have a data entry function. Only listening to traffic and displaying words on the screen. I wouldn’t want every second person to start terrorizing the described applications and increasing their ratings. Moreover, before the publication of this issue of the journal, the authors of the applications were informed about the presence of the vulnerability, which will likely lead to its elimination. If you want to repeat something similar to the picture below, then please write the missing function for answering the questions yourself.
This is what happened in the end
Advantages and disadvantages
As you can understand, this method of boosting drugs has both advantages and disadvantages. Below I have highlighted the main ones. The advantages include:
- Very fast turnaround. Much faster than using various services or offers. Messages are processed instantly, and the procedure itself takes no more than a minute.
- Endless cheating. The number of added drugs is limited only by the capabilities of the VK website interface.
- No third party software required. You don’t need to register and complete tasks on various exchanges for the mutual exchange of activity, you don’t need to download and configure bots, you don’t need to spam in groups like “Clog LAN,” etc. All you need is to log into VK through any browser.
- For free. Unlike cheating with third-party software, you don’t have to pay here.
The disadvantages include:
- Imaginary popularity. When you use the page element code, no real messages are sent to you. You just change the number next to the menu item. Therefore, if you need to take a screenshot of the dialogues, and not the “New messages” numbers, then this method will not suit you.
- Changes are not saved. You do not send information to the VK servers, you only change the page code in your browser. After completing the session (updating or closing the tab), the changes will disappear. But this also leads to a plus - this method is safe and does not lead to a ban (unlike the same third-party services).
We recommend reading “5 groups and other ways to boost messages without tasks and for free on VK.”
And it's all?
And this will be a completely appropriate question. The presence of a vulnerability of this class is not limited to just one application. By the way, the entire cycle of applications of this developer is subject to this kind of cheating. Namely:
- Linguamania;
- Quiz;
- Guess the melody;
- Photo Quiz;
And also some others.
A superficial search among VKontakte applications yielded several more fruits. The first one is the Bubbles app.
Game "Bubbles"
If you are a good algorithmist and can write a decent program to score the maximum number of points on a given field, then there is great news for you. The layout of the “clearing” before your eyes:
This is what Neo saw in the Matrix
Sudoku lovers have their own place on VKontakte.
This is the schedule
All that is required here is a good and fast algorithm for solving the problem, fortunately its condition does not need to be obtained by recognizing the image on the screen, just look at the traffic.
As you, I hope, understand, the variety of VKontakte applications is not comparable with the quota allocated for the article, so I leave the search for potential victims to you, dear reader, as homework.
Possible problems
There are not many problems that users may encounter when using DM promotion through the element code. But let's look at those that are:
- Accidental or intentional page refresh, after which all changes disappear. You can always do the procedure again, but still be careful and try not to refresh or close the tab.
- A screenshot that will give you away. Often, using this method, people take a screenshot of a page with dialogues. And there, as you might understand, there are no new messages. Be careful when taking a screenshot and open another page of the VK website in advance (since after cheating it will not be possible to update the page).
- Difficult to find the right element. This is one of the most common problems. Users open the code in an arbitrary place on the page, and then cannot find the element they need. To avoid this error, click with the second mouse button on the “New messages” number. As a last resort, use the method I described earlier (instructions, step 4).
Bottom line
Today we talked to you about how to generate messages in VK through the page element code. This is a simple and easy way to wipe the noses of your envious people. But still remember that such popularity is not real.
Read further:
How to create messages on VK for free and quickly, without causing headaches?
5 groups and other ways to boost messages without tasks and for free on VK
How and what can you change in VK messages?
Script for boosting VKontakte messages: how to use it?
We wind up messages in VK without letting go of the phone
[Total: 0 Average: 0/5]
Author of the publication
offline 3 years
Summing up
In conclusion, let's think about who is to blame and what to do. Blame is found on the laziness and thirst for profit of application developers, as well as the selfishness of those who use these applications, sitting all night long and growing a “virtual genital organ.” Otherwise, these applications simply would not be developed for the general public. Of the ways to solve the problem that I personally see, I will suggest the following.
For developers. Take a closer look at the security of using applications. The introduction of simple “encryption” with a shift of a couple of bytes should already discourage a significant proportion of “hackers” from delving into the traffic, not to mention more advanced methods of data protection, which, depending on your imagination, will, to one degree or another, protect the application from inadequate user actions.
Burglars. There is no point in hoping that a serious fish with security gaps such as those described above will be hooked. Developers of large applications (especially those where the presence of a monetary component is felt) usually know how to calculate losses from the activities of those who like to “dig inside”. So take all of the above into account without any unnecessary illusions regarding the extremely beneficial application of this knowledge in practice.
For those who are still playing. Stop doing that. These are just dots on the screen. In many games there is a very real possibility of automating the game process and all your many hours, and in rare clinical cases, many days, efforts will look meager compared to the results of the computer program. The program does not want to sleep or eat. She doesn't get tired and doesn't give up. There is no need to compete with the program. Live a real life, not the life of a “level 80 elf.” Having experienced all this at one time from personal experience, I quit doing it. And so, realizing that knowledge was worth sharing with others, I opened a text editor and wrote the first lines of this article.